Front-End Development in 2025: Challenges, Trends, and Accessibility
- January 13
- 8 min

A frontend security framework acts as the primary shield for your web applications and everyone who uses them. By design, a user’s browser is an untrusted space where any code can be manipulated. Overlooking frontend security exposes sensitive user data, threatens your application’s integrity, and ultimately destroys user trust. A solid framework gets ahead of these issues by focusing on the source: how data is handled, how user actions are verified, and how the app communicates with backend services. It embeds security into the core development process instead of treating it as an afterthought, effectively neutralizing the most frequent and harmful web attacks.
Cross-Site Scripting, better known as XSS, is a sneaky injection attack. It works by slipping malicious scripts into websites that users already trust. Once there, the script executes in a victim’s browser, letting the attacker bypass security, swipe session cookies, or even change what’s on the page. To stop XSS for good, you need a defense with multiple layers; a single trick just won’t cut it.
Input sanitization and validation are your first and most basic defenses against XSS. Sanitization involves scrubbing user-submitted data, stripping out or neutralizing dangerous elements like script tags. At the same time, validation checks that the input matches an expected format—like a valid email or a specific number pattern. While client-side validation is great for user experience because it offers instant feedback, it’s easily bypassed by a determined attacker. That’s why all critical validation must happen on the server before you ever process or save the data; client-side checks are just a helpful first screen.
function sanitizeInput(input) { const div = document.createElement('div'); div.textContent = input; return div.innerHTML;}// Example usage:// let maliciousInput = "<script>alert('XSS');</script>";// let cleanInput = sanitizeInput(maliciousInput);// console.log(cleanInput); // Output: <script>alert('XSS');</script>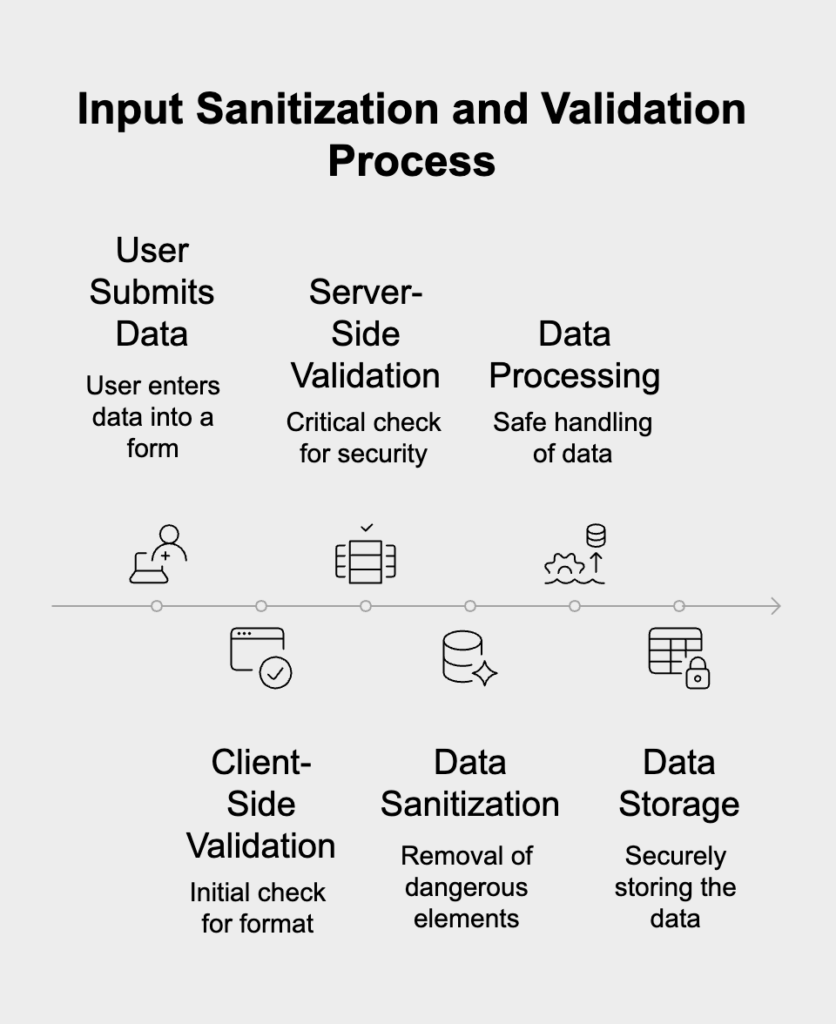
Output encoding is the step that guarantees data shows up on a page as simple text, not as code the browser can run. This is your safety net. Even if a malicious script somehow slips past your validation and into your database, proper encoding stops the browser from ever executing it. The process works by converting special characters into their HTML entity equivalents—for instance, the character < becomes < and > becomes >. This simple transformation renders the malicious code completely inert, forcing the browser to display it as harmless text instead of running it.
A Content Security Policy (CSP) adds a powerful layer of security through a simple HTTP response header. It gives you precise control over which resources a browser is permitted to load for your page. By creating a whitelist of trusted sources, a CSP can stop browsers from loading malicious scripts injected through an XSS attack, even if your other defenses fail. For example, you can tell the browser to only allow scripts from your own domain and a specific CDN, which blocks all inline scripts and anything from an unknown source.
A Cross-Site Request Forgery (CSRF) attack tricks an authenticated user’s browser into making an unwanted request to your application. Since the request comes from the user’s browser and carries their valid session cookies, your server sees it as legitimate. This can trick the server into performing sensitive actions like changing the user’s email, transferring money, or deleting an account—all without the user’s knowledge.
Anti-CSRF tokens are the go-to defense against these attacks. Using what’s known as the synchronizer token pattern, your application embeds a unique, secret, and unpredictable value into every form that can change the application’s state. When a user submits that form, the token is sent back to the server. The server then checks if the submitted token matches the one it generated for that user’s session. An attacker can’t guess this secret token, so any forged request they create will be missing it and get rejected instantly.
Setting up your cookie attributes correctly gives you a powerful second layer of defense against CSRF. Two attributes are especially important:
SameSite=Strict stops the cookie from being sent on any cross-site request, which shuts down CSRF completely, while SameSite=Lax provides a good mix of security and usability by blocking it for most third-party-initiated requests,
Protecting data on the frontend means securing any sensitive information handled or sent by the client-side of your app. This covers everything from user credentials and personal details to session data. The main goal is to keep data safe in the browser and during transit, ensuring only the right people can access the right features.
Strong authentication begins with a solid password policy, demanding a minimum length and a mix of uppercase letters, lowercase letters, numbers, and symbols, while also blocking common passwords. Sessions need to be managed just as carefully. Always generate session IDs with high entropy, destroy them on logout or after a timeout, and store them in secure, HttpOnly cookies. This last step is vital for preventing XSS attacks from stealing the session token.
// Example of a basic password strength regex in JavaScriptfunction isStrongPassword(password) { // Requires at least 8 characters, one uppercase, one lowercase, one number, one special character const strongPasswordRegex = new RegExp("^(?=.*[a-z])(?=.*[A-Z])(?=.*[0-9])(?=.*[!@#$%^&*])(?=.{8,})"); return strongPasswordRegex.test(password);}Real access control boils down to one rule: never trust the client. Hiding buttons or links on the frontend is great for usability, but it isn’t actual security. Every single request for a sensitive page or API endpoint has to be authenticated and authorized on the backend before any action is taken or data is sent. This server-side check is what stops a savvy user from just guessing an API URL and gaining access they shouldn’t have. Furthermore, all this communication must be protected in transit. Using HTTPS (Hypertext Transfer Protocol Secure) is non-negotiable, as it encrypts the entire data stream between the browser and the server with TLS. This encryption blocks man-in-the-middle (MITM) attacks, preventing anyone from snooping on or tampering with sensitive info like passwords or credit card details.

Beyond tackling specific threats like XSS and CSRF, a complete security framework needs a few more key practices to harden the application and keep security top-of-mind. For starters, modern web apps are built on countless third-party libraries from registries like npm, and every single one is a potential backdoor. Vulnerabilities can pop up in any dependency at any time. That’s why you must regularly scan your dependencies for known issues using tools like `npm audit` or other scanners. Just as critical is having a plan to quickly update or patch those libraries as soon as a flaw is found.
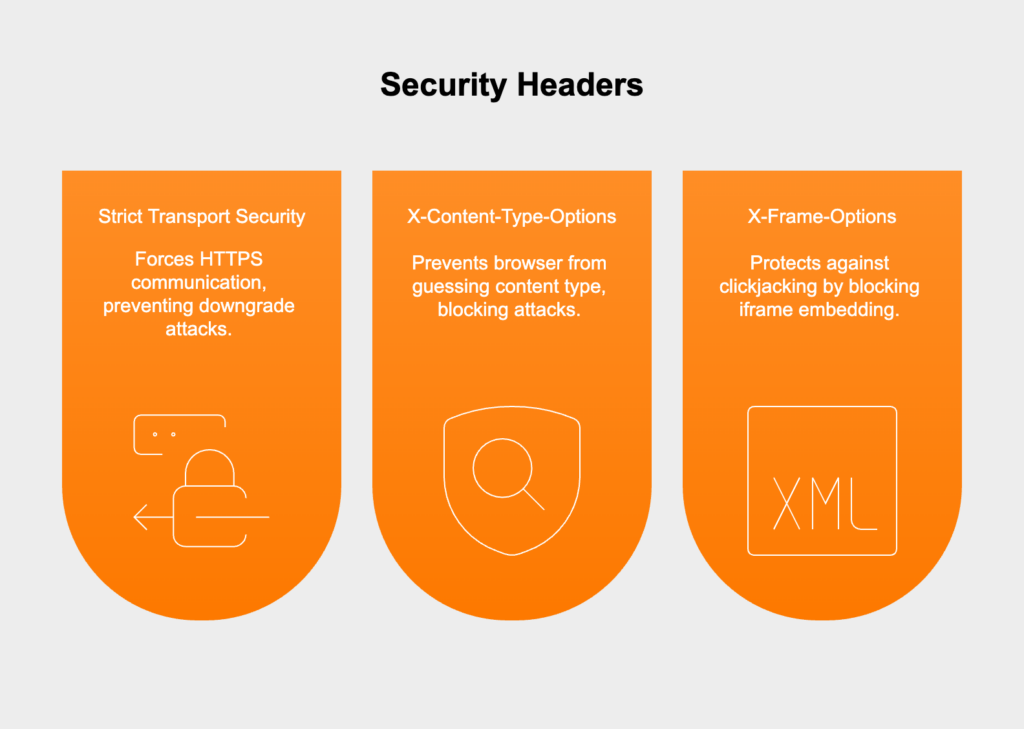
On top of a Content Security Policy, a few other HTTP headers can add critical security with very little effort: