Don’t worry – there is a Progressive Web App for that!
- June 22
- 5 min

The Open Web Application Security Project (OWASP) Top 10 is the recognized global standard for pinpointing and neutralizing the most critical security risks web applications face. For anyone in development, security, or compliance, this isn’t just another list of vulnerabilities—it’s the bedrock framework for building secure software. Using the OWASP Top 10 to build a security checklist gives you a systematic, risk-based plan for hardening your applications against common attacks.
But aligning with the OWASP Top 10 isn’t just good security hygiene; it’s also a major step toward satisfying tough regulatory requirements. Key regulations like the Payment Card Industry Data Security Standard (PCI DSS), the General Data Protection Regulation (GDPR), and the Health Insurance Portability and Accountability Act (HIPAA) all demand that organizations implement strong security controls. An OWASP-based checklist gives you a practical roadmap to meet these technical demands, helping you demonstrate due diligence and build a defensible security posture.
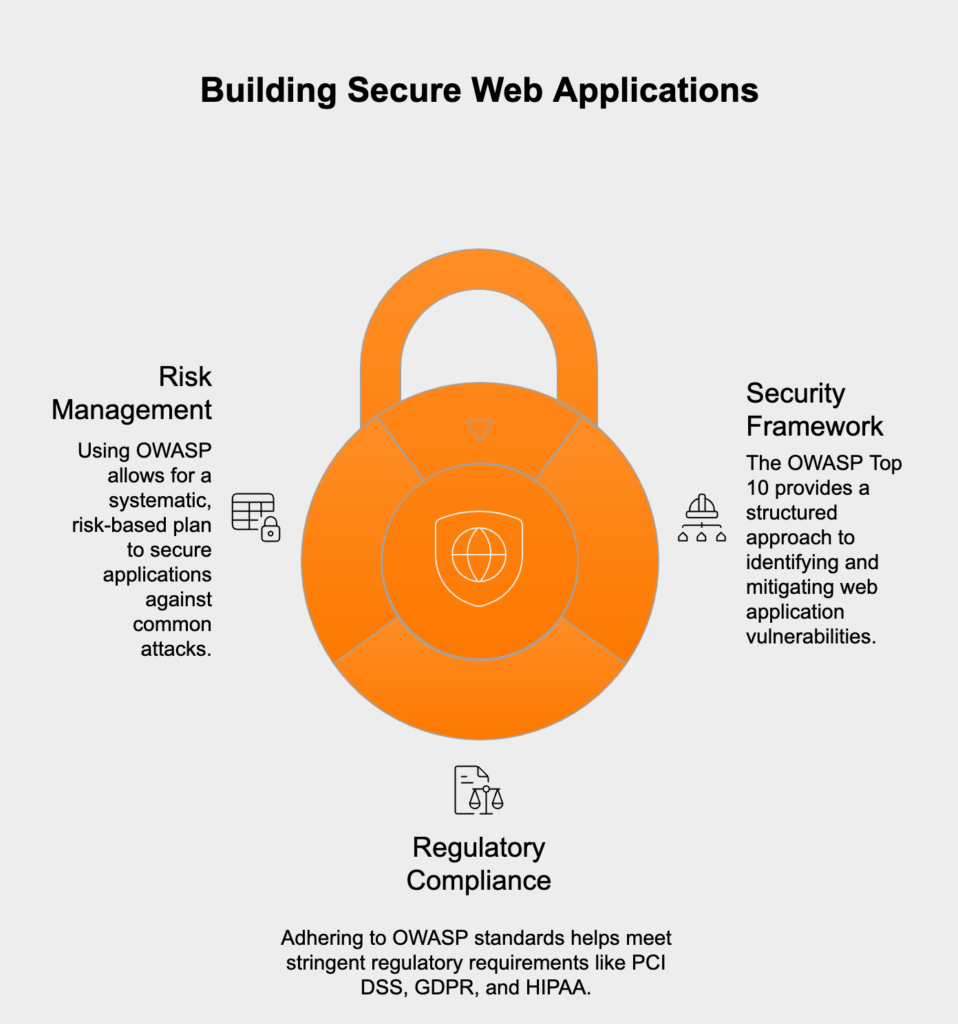
A solid web application security program starts with a detailed, actionable checklist built on the latest OWASP findings. Here, we’ll break down each of the ten risks from the 2021 list, with practical steps for verification and a clear line to key compliance rules. This approach helps teams systematically test, fix, and document their security controls.
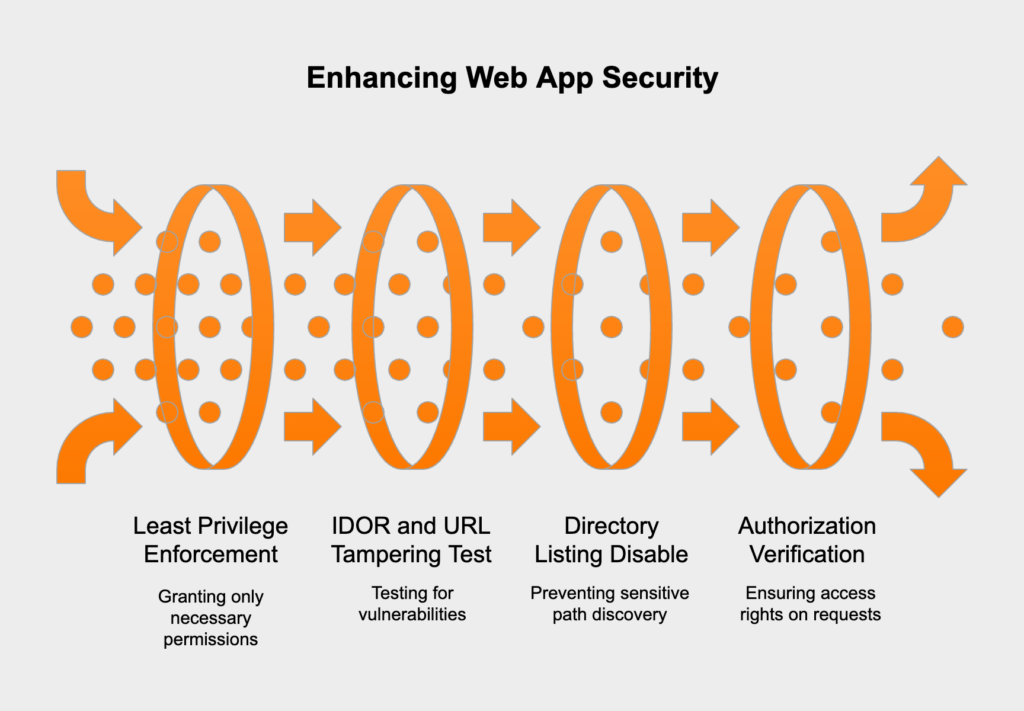
Broken access control happens when you don’t properly enforce what authenticated users are allowed to do. Attackers exploit these gaps to get at functionality or data they shouldn’t, like other users’ accounts, sensitive files, or private data. Your controls have to guarantee that users can’t step outside their assigned permissions.
Compliance Impact: This directly addresses requirements in PCI DSS 7 (Restrict access to cardholder data by business need to know), GDPR Article 25 (Data protection by design and by default), and HIPAA 164.312(a) (Access control).
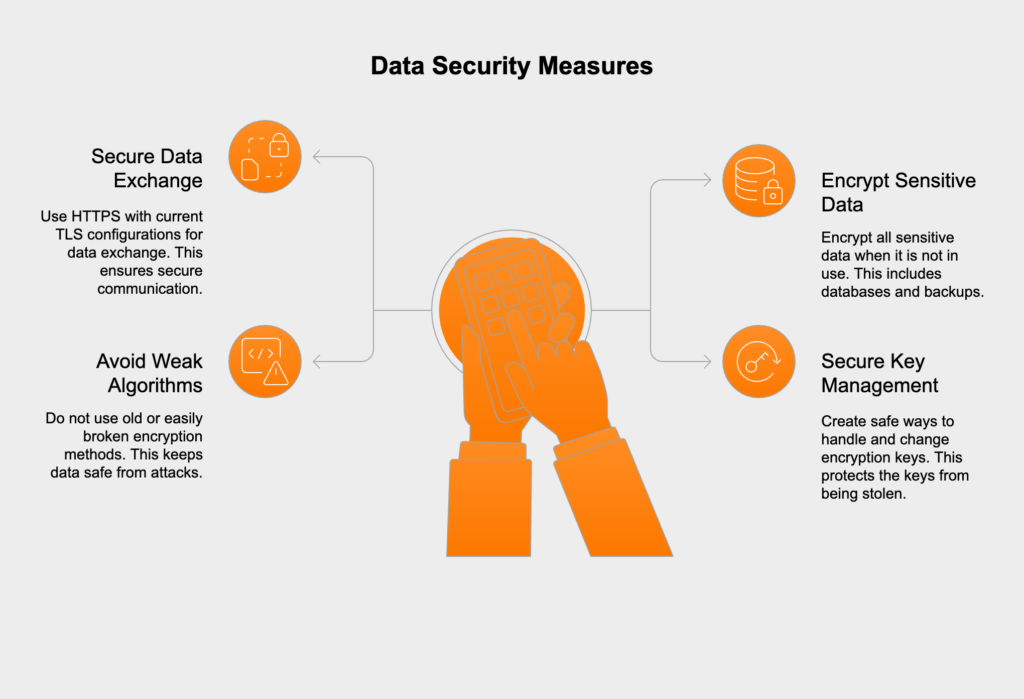
This category, which used to be called “Sensitive Data Exposure,” covers failures in cryptography that expose sensitive data. This applies to data both in transit across the network and at rest in storage. To get this right, you must use strong, modern encryption standards wherever you handle sensitive information.
Compliance Impact: Strong cryptography is a core requirement of PCI DSS 3 & 4 (Protect stored and transmitted cardholder data), GDPR Article 32 (Security of processing), and HIPAA 164.312(e) (Transmission security and encryption).
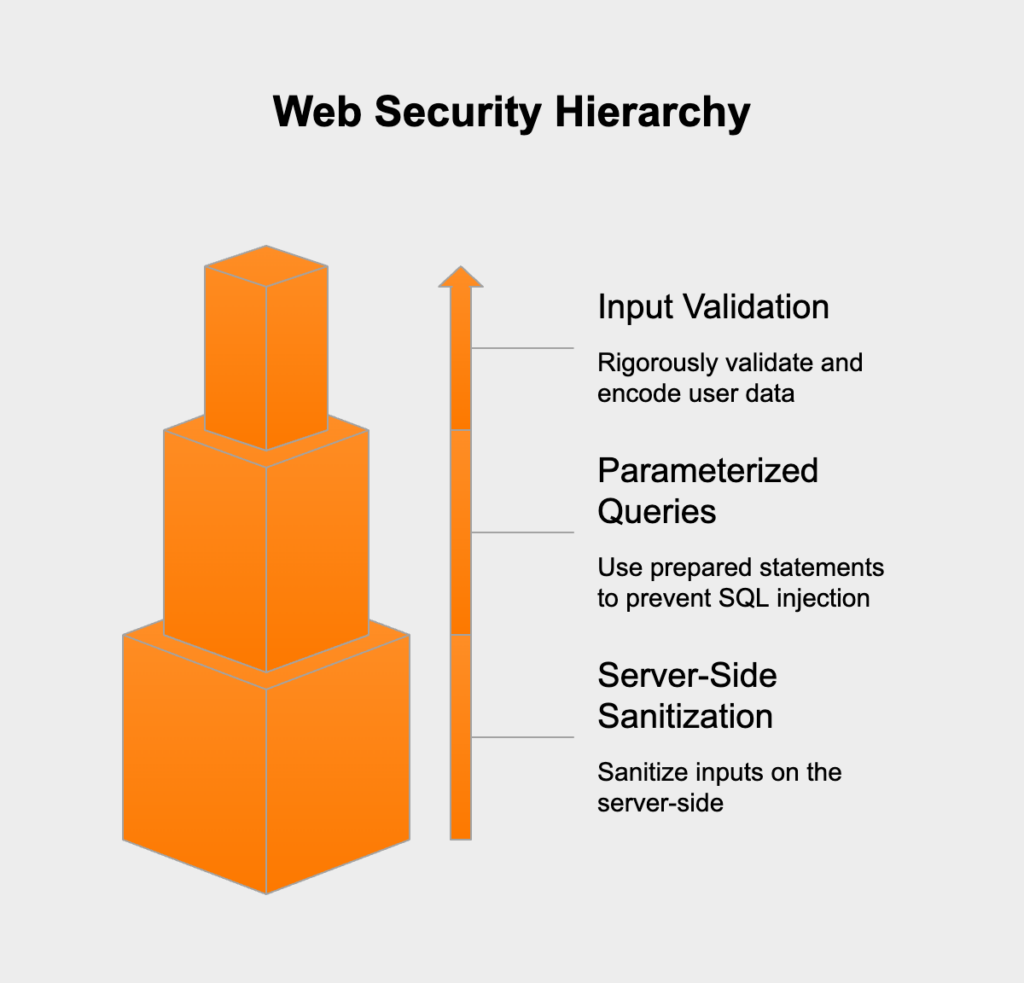
Injection flaws like SQL, NoSQL, command injection, and Cross-Site Scripting (XSS) happen when untrusted data gets sent to an interpreter as part of a command or query. An attacker’s malicious data can trick the interpreter into running commands it shouldn’t or accessing data without permission. The key to prevention is simple: treat all input as untrusted.
Compliance Impact: Preventing injection is fundamental to secure coding practices mandated by PCI DSS 6.5 (Address common coding vulnerabilities), GDPR Article 32, and HIPAA 164.308(a) (Security Management Process).
This is a broad category for weaknesses that come from a lack of security-focused design—not a bug, but a flaw in the architecture itself. Unlike a simple coding mistake, these vulnerabilities are baked in from the start because of missing or weak security controls. Fixing this means taking a proactive approach to security throughout the entire development lifecycle.
Compliance Impact: This aligns with process-oriented requirements like PCI DSS 6.3 (Develop applications securely), GDPR Article 25, and HIPAA 164.308(a).
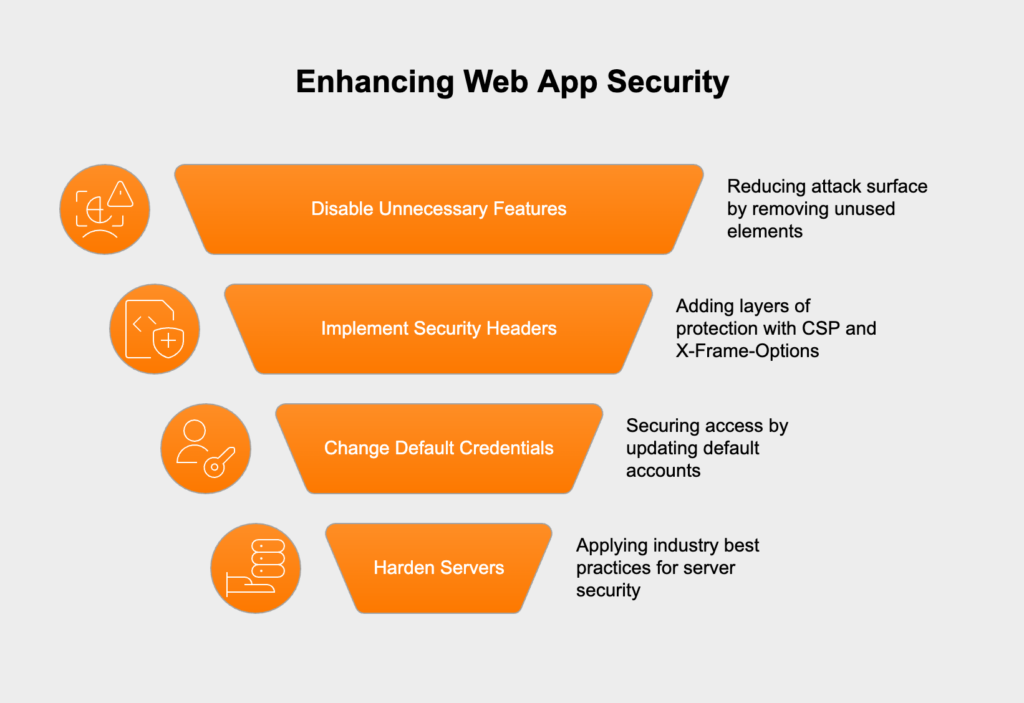
As one of the most common vulnerabilities, security misconfiguration can pop up anywhere in the application stack—the network, platform, web server, or the app itself. Typical mistakes include leaving default credentials active, enabling features you don’t need, and showing overly detailed error messages that leak internal information.
Compliance Impact: Regulations like PCI DSS 2 (Do not use vendor-supplied defaults), GDPR Article 32, and HIPAA 164.308(a) all explicitly require secure configuration.
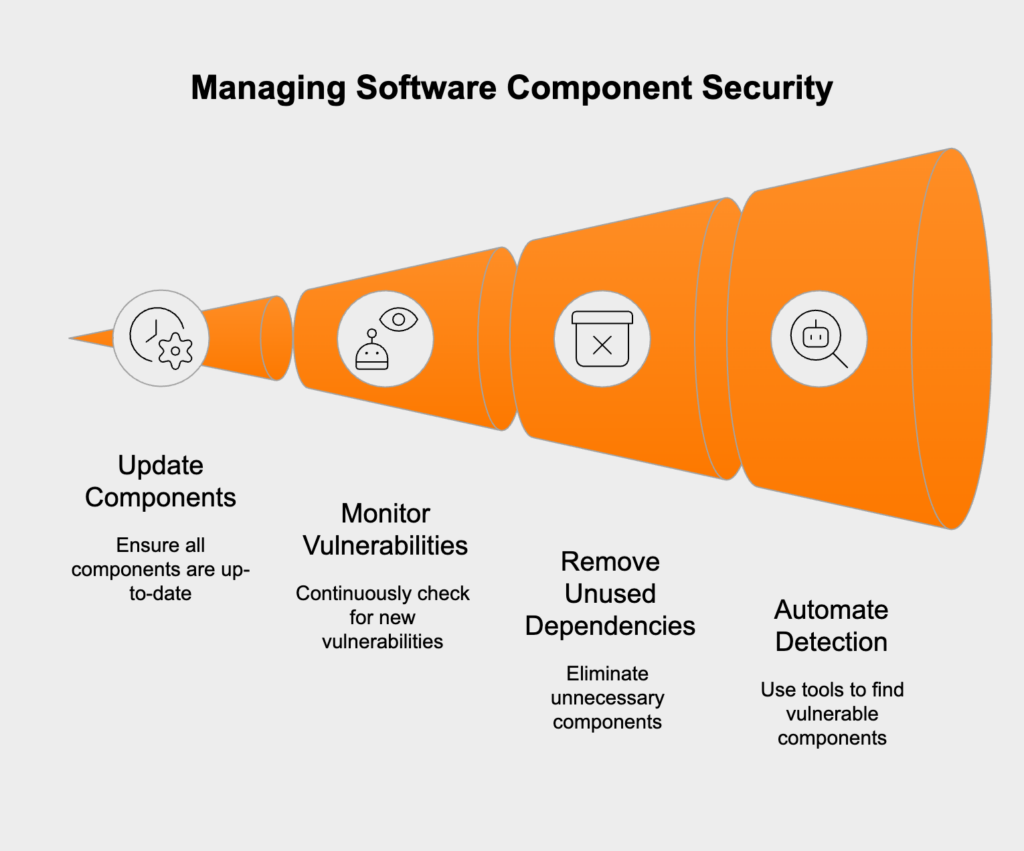
Today’s applications are built with tons of third-party libraries, frameworks, and other components. If a vulnerability is found in one of those components, every application using it is suddenly at risk. Attackers are constantly scanning for systems running unpatched or outdated components to exploit these known flaws.
Compliance Impact: Patch management is a core tenet of PCI DSS 6.2 (Protect all system components from known vulnerabilities), GDPR Article 32, and HIPAA 164.308(a).
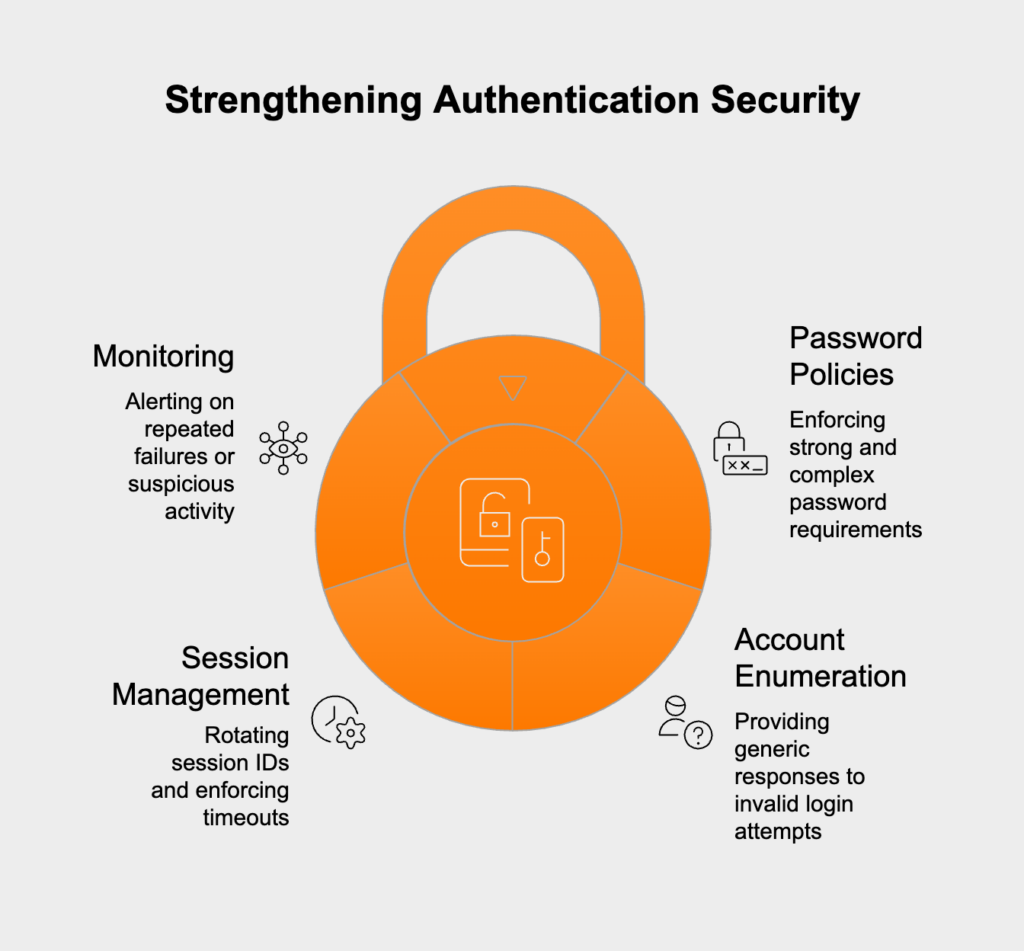
When authentication and session management are implemented poorly, attackers can compromise user accounts, passwords, and session tokens. This allows an attacker to impersonate real users, either for a moment or forever, and get unauthorized access to your system.
Compliance Impact: You’ll find mandates for strong authentication in PCI DSS 8 (Identify and authenticate access), GDPR Article 32, and HIPAA 164.308(a).
This category is all about vulnerabilities that compromise the integrity of your software updates, critical data, and CI/CD pipeline. A failure here means an attacker could inject malicious code or corrupt sensitive data. A prime example is insecure deserialization, where an application processes hostile data without checking its integrity, which can lead to remote code execution.
Compliance Impact: This is covered by controls in PCI DSS 6.5, GDPR Article 32, and HIPAA 164.312(c) (Integrity).
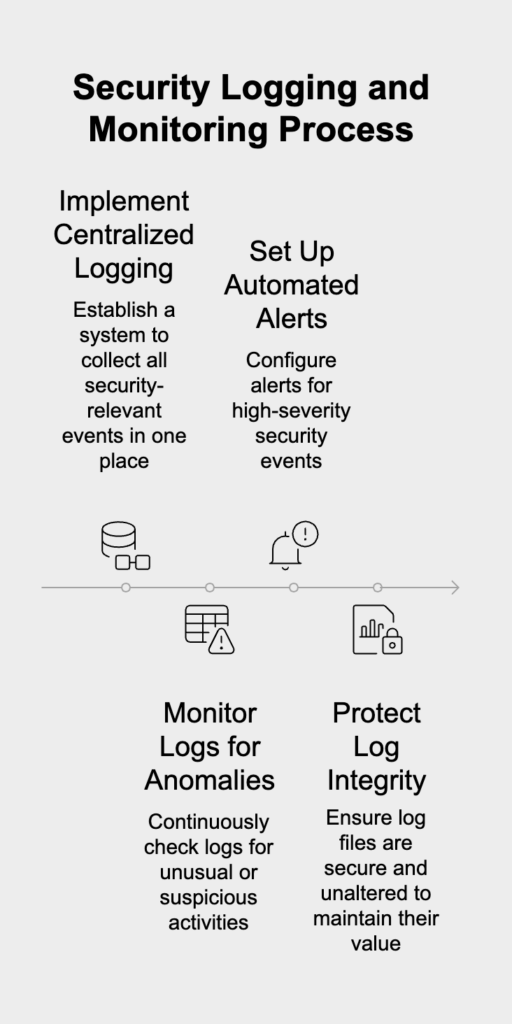
Without enough logging and monitoring, it’s almost impossible to spot an ongoing attack or conduct a forensic investigation after a breach. Failing here gives attackers more time inside your system to do damage and steal data before you even know they’re there.
Compliance Impact: Meeting the requirements of PCI DSS 10 (Track and monitor all access), GDPR Article 33 (Notification of a personal data breach), and HIPAA 164.308(a) is impossible without proper logging and monitoring.
An SSRF flaw happens when a web application fetches a remote resource but doesn’t properly validate the URL supplied by the user. This lets an attacker trick the application into sending a crafted request to an unexpected place—even to internal-only services behind your firewall. The result can be anything from information leaks to direct interaction with your internal systems.
Compliance Impact: SSRF prevention falls under secure coding principles in PCI DSS 6.5, as well as general security measures required by GDPR Article 32 and HIPAA 164.308(a).
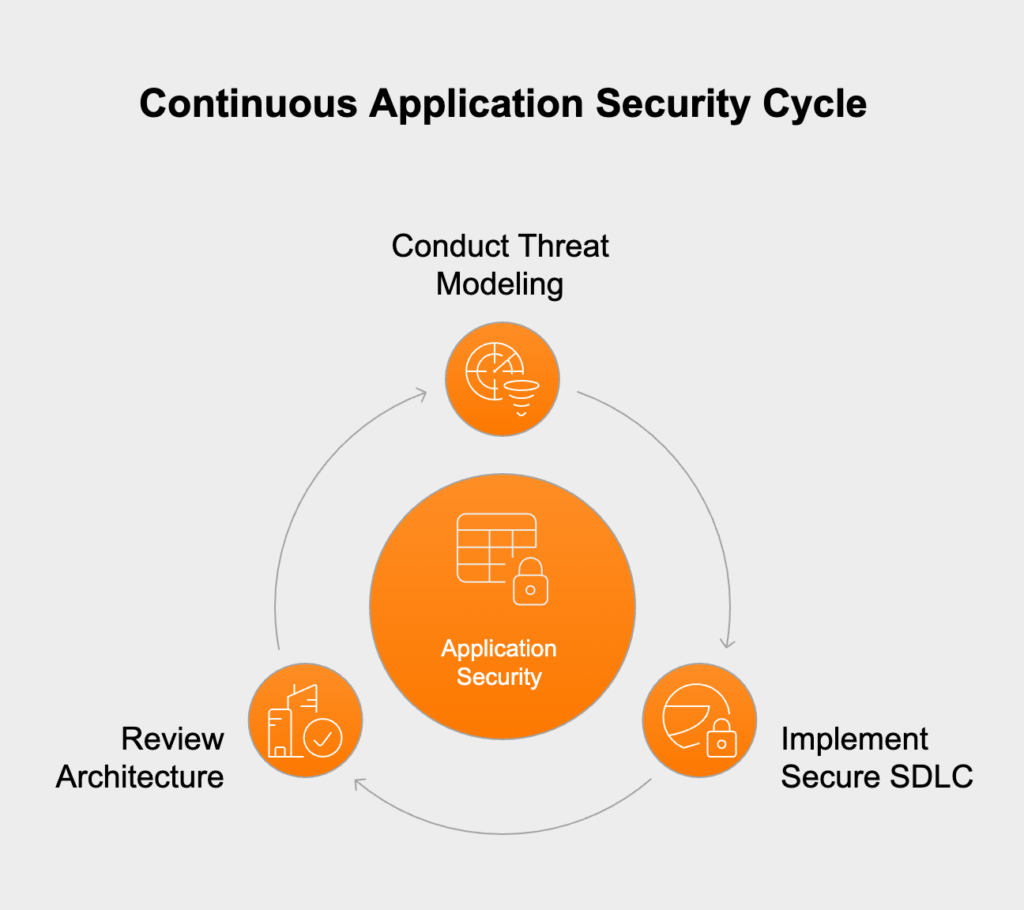
A static OWASP Top 10 checklist is a great start, but it’s most effective as part of a continuous security program. Instead of just running occasional checks, true security means building it into your team’s culture and daily development process. This requires a multi-pronged approach: proactive design, tough validation, and constant vigilance.
The best way to eliminate vulnerabilities is to stop them from ever being introduced. That’s the core idea behind Insecure Design (A04) and the “shift left” security movement. Threat modeling is a critical practice where your team brainstorms potential threats, attack vectors, and misuse cases *before* a single line of code is written. By thinking like an attacker and anticipating how they might target the app’s logic or architecture, developers can build in the right defenses from the ground up, creating a much more resilient system.
Checklists and automated scanners are great for finding known vulnerabilities, but they can’t match the creativity and intuition of a human attacker. Penetration testing is the ultimate reality check for your security controls. Professional testers simulate real-world attacks, finding weaknesses that automated tools miss, like complex business logic flaws or chained exploits. A good penetration test will actively try to break the controls on your OWASP checklist, giving you the hard proof that your defenses work under pressure, not just on paper.
No security program can prevent 100% of attacks. That’s why strong detection and response capabilities are non-negotiable. This directly tackles Security Logging and Monitoring Failures (A09) by giving you visibility into what’s happening across your application. A mature program needs centralized logging, automated alerts for suspicious events, and a well-defined incident response plan. By constantly watching for abnormal activity and being ready to act fast, you can minimize the damage from a potential breach and meet the notification deadlines required by regulations like GDPR and HIPAA.
