11 DevOps Maturity Assessment Questions to Ask During the Audit
- April 02
- 6 min

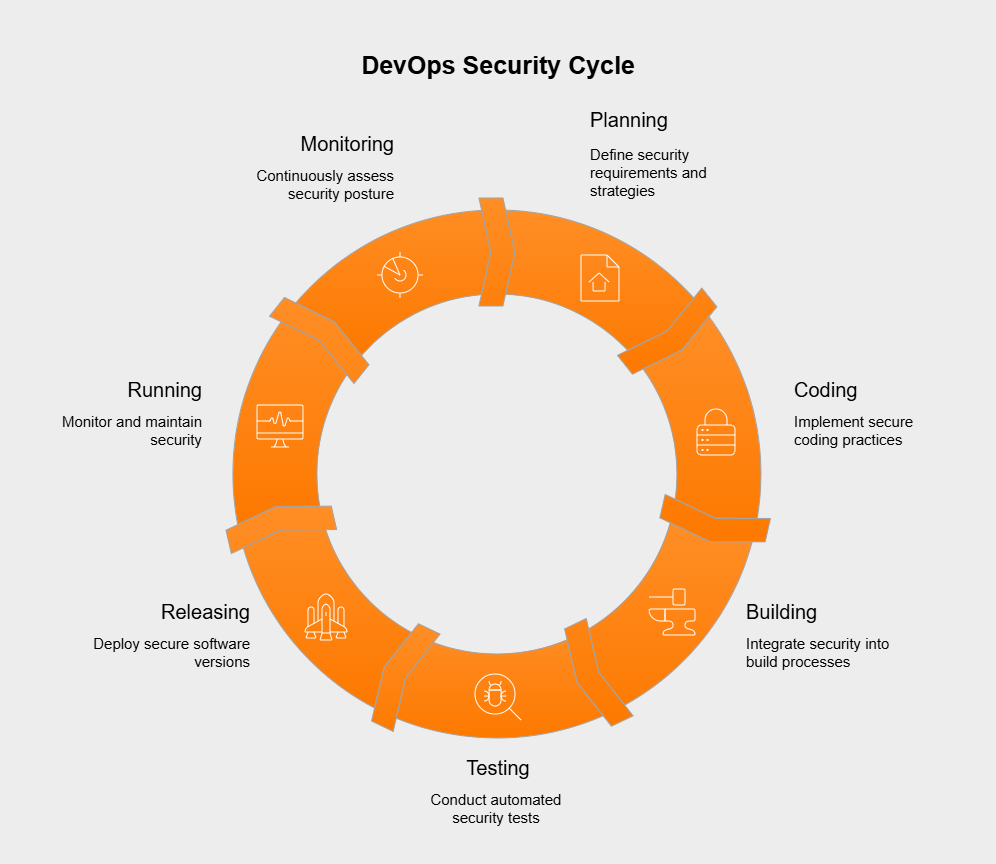
DevOps security, often called DevSecOps, means embedding security practices, ways of thinking, and tools right into every step of the DevOps pipeline. It’s a big change from older methods where security was tacked on at the end. Instead, security becomes everyone’s job, woven through the whole software development lifecycle (SDLC) – from planning and coding to building, testing, releasing, running, and watching the software. The main goal is to make security a natural part of how development and operations work, not a roadblock.
This way, security thinking happens right from the start (“shifting left”), and tasks get automated whenever possible to keep up with how fast modern teams build software. It builds a culture where developers, operations folks, and security experts work closely together, all responsible for creating and keeping applications and infrastructure safe. Ultimately, DevOps security strives to deliver software that doesn’t just work well but is secure from the ground up.
DevOps security is quite different from traditional security models. Typically, older approaches treated security as a separate step handled late in the development cycle. A security team would often check things only after most development was done, which could cause delays and expensive fixes if problems were found late.
Here are the key differences:
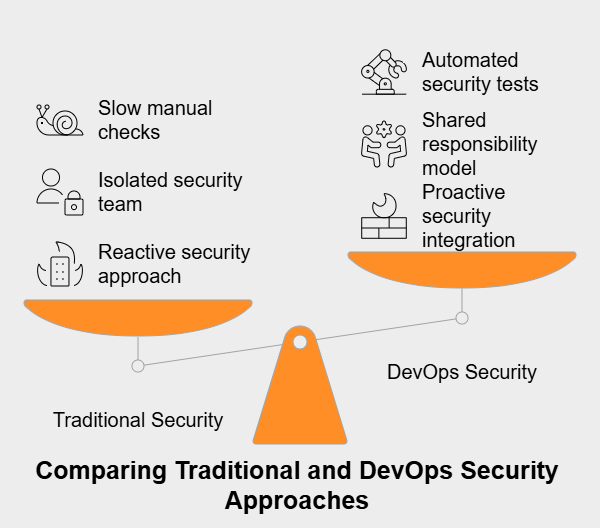
Several core ideas shape how DevOps security is put into practice, aiming to weave security thinking throughout the software delivery process.
The “shift left” idea means moving security checks, tests, and thinking to the very beginning of the SDLC. Rather than waiting until the end, security activities like code scanning, checking dependencies, and threat modeling happen during requirements, design, and coding. The biggest advantage is catching vulnerabilities early – that’s when they are much simpler, faster, and cheaper to fix. Dealing with security issues early stops them from spreading and keeps delivery schedules on track.
Automation is key to fitting security into fast DevOps workflows without slowing things down. Many security tasks that used to be manual are now automated and built right into the CI/CD pipeline. Think automated static application security testing (SAST) when code is checked in, dynamic application security testing (DAST) in test environments, automated scans for known issues in dependencies and container images, and automated checks for configuration and compliance rules. Automation makes sure security controls are applied consistently and gives quick feedback to development teams.
Continuous monitoring keeps watch over security even after software is deployed and running. It uses automated tools and processes to constantly observe live applications and infrastructure, looking for signs of security threats, strange behavior, wrong configurations, or active attacks. This involves analyzing logs, detecting intrusions, monitoring performance with a security focus, and sending real-time alerts. Continuous monitoring allows for quick reactions to security incidents and helps protect live systems, feeding information back into the development cycle for ongoing improvements.
Breaking down the old walls between development, operations, and security teams is central to DevOps security. Better collaboration helps everyone see security not as a hurdle, but as a vital part of delivering quality software. When teams talk effectively and share the load, security needs are understood better and included earlier, security tools get adopted more easily, and responding to incidents becomes smoother. This change in mindset creates a shared sense of ownership for the security posture.
Security as code takes the ideas from infrastructure as code (IaC) and applies them to managing security. It means defining security rules, controls, settings, and compliance needs in code files that are stored in version control, instead of using manual setups or documents. This lets security measures be automatically set up, tested, reviewed, and enforced consistently across different environments. Treating security configurations like application code makes security practices more transparent, repeatable, easy to audit, and scalable.
Putting DevOps security into action involves using a mix of specific tools, methods, and processes integrated across the SDLC. A key early step is threat modeling, a systematic way to identify potential security threats, weaknesses, and attack paths during the design and planning stages. Thinking like an attacker from the start allows teams to build in security controls proactively, avoiding the need for costly fixes later on.
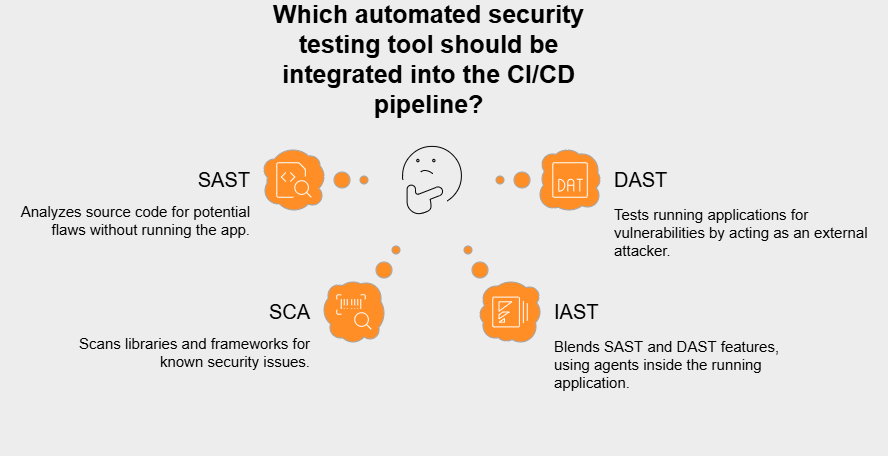
Various automated testing tools get plugged into the CI/CD pipeline to give constant feedback on security health. Important types include:
Strong access control is crucial. This means following the principle of least privilege—giving users and systems only the minimum permissions they absolutely need. Privileged access management (PAM) tools help control, monitor, and secure accounts with high-level permissions. Doing regular access reviews and using role-based access control (RBAC) also helps tighten security.
Beyond the initial tests, vulnerability management never stops. It involves constantly scanning environments (like code repositories, container registries, live infrastructure) for new weaknesses, judging their risk based on severity and context, setting priorities for fixing them, and tracking the progress. This cycle helps keep systems safe from newly discovered threats.
Since setting up infrastructure is increasingly automated with Infrastructure as Code (IaC) tools (like Terraform, CloudFormation, Ansible), securing the templates and configurations they use is vital. This means scanning IaC templates for bad configurations, security policy breaches, and hidden secrets before they get deployed. Secure coding habits need to apply to IaC development just like they do for application code.
Handling sensitive data like API keys, passwords, and certificates—known as secrets—securely is critical in automated systems. Secrets management uses special tools (like HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) to store secrets safely, strictly control who can access them, allow for rotation, and inject them into applications or infrastructure automatically when needed, preventing them from being hardcoded in files.
Today’s applications lean heavily on third-party libraries and open-source code. Software supply chain security is all about managing the risks that come with these outside dependencies. Good practices include checking components before using them, using SCA tools to scan for known vulnerabilities, making sure build processes are secure, and potentially using artifact repositories that enforce rules about which components are allowed.
A strong DevOps security culture needs knowledgeable teams. Regular security training and awareness efforts are essential for developers, operations staff, and testers. This covers teaching secure coding methods, common vulnerabilities (like the OWASP Top 10), threat modeling skills, and how to use security tools correctly, helping everyone play their part in security.
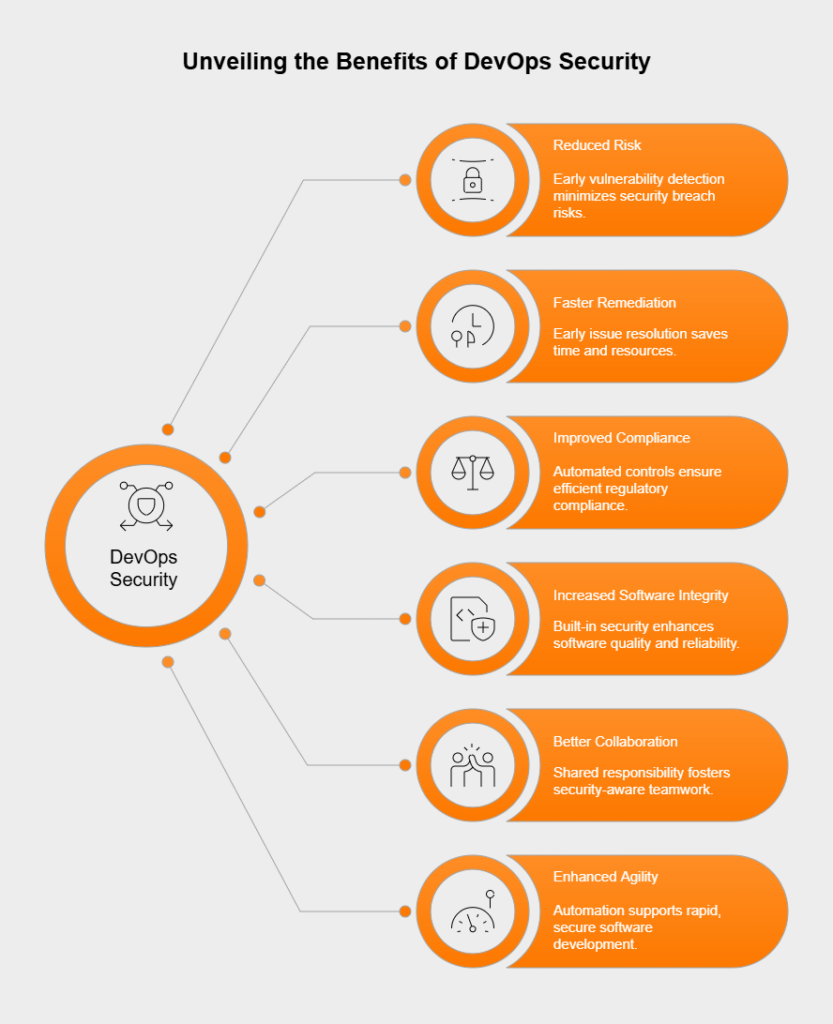
Bringing security into DevOps practices gives organizations major advantages, improving both the speed and safety of software delivery.
While very beneficial, moving to a DevOps security model can bring several hurdles:
DevOps security streamlines compliance and governance using automation and integration. Security policies and compliance rules can be written as code (Policy as Code) and automatically enforced in the CI/CD pipeline and live environments. Continuous monitoring and automated checks give real-time insight into security status and compliance, making reporting and audit evidence gathering much simpler. Tools can automatically verify configurations against known standards (like CIS Benchmarks) or regulations (like PCI DSS, HIPAA). This organized, automated method ensures security governance is applied consistently and can be audited throughout the software lifecycle.
Yes, DevOps security increasingly embraces Zero Trust thinking. A Zero Trust approach works on the idea that threats might be anywhere, inside or outside the network, so no user or system gets trusted automatically. In DevOps, this means setting up strict identity checks for developers, tools, and services accessing the pipeline, enforcing least privilege access for code repositories, build systems, and deployment areas, dividing networks and workflows, and constantly monitoring activities for anything suspicious. Applying Zero Trust strengthens the security of the entire development and delivery process by getting rid of assumed trust and checking every access request carefully. If you need support in shaping your DevOps, get in touch!
